
AEC data is valuable—drawings, models, contracts, site details. Attacks keep rising and losses are real: the FBI logged $16B in reported cyber losses for 2024, up 33% year over year (FBI/IC3; Reuters). Phishing pretexting continues to drive breaches (Verizon DBIR). Your virtual team, partners, subcontractors, and assistants add speed, but also expand the attack surface. This guide shows where AEC firms get hit, how to harden cloud workflows, and the exact steps to deploy: MFA, role-based access, training, backups, CDE hygiene, and a 24-hour incident playbook for strong cybersecurity for AEC remote teams. Every claim links to a public source so you can verify and act.
AEC files reveal layouts, systems, and client data. That’s sensitive and profitable for attackers. A recent AEC Data Insights Report from Egnyte (2024) paints a troubling picture of the industry’s cybersecurity resilience. Nearly eight out of ten firms (77%) admit they couldn’t function beyond five days if locked out of their files during a ransomware incident. Yet, recovery from such attacks often stretches past the 20-day mark, leaving project schedules and client commitments in jeopardy.
The risk isn’t hypothetical; it’s happening. Over the last two years, 59% of AEC organizations have suffered some form of cybersecurity breach. General contractors have been hit hardest: 70% reported at least one cyber event, and 30% faced ransomware directly since 2021.
Ransomware continues to disrupt critical sectors and lock operations. In distributed AEC teams, with outsourced staff, consultants, and many cloud tools, one weak account can expose an entire project.
Business impact
AEC firms face serious cybersecurity threats due to distributed teams, shared cloud platforms, and sensitive project data. Below are the most common risks, summarized clearly and practically.
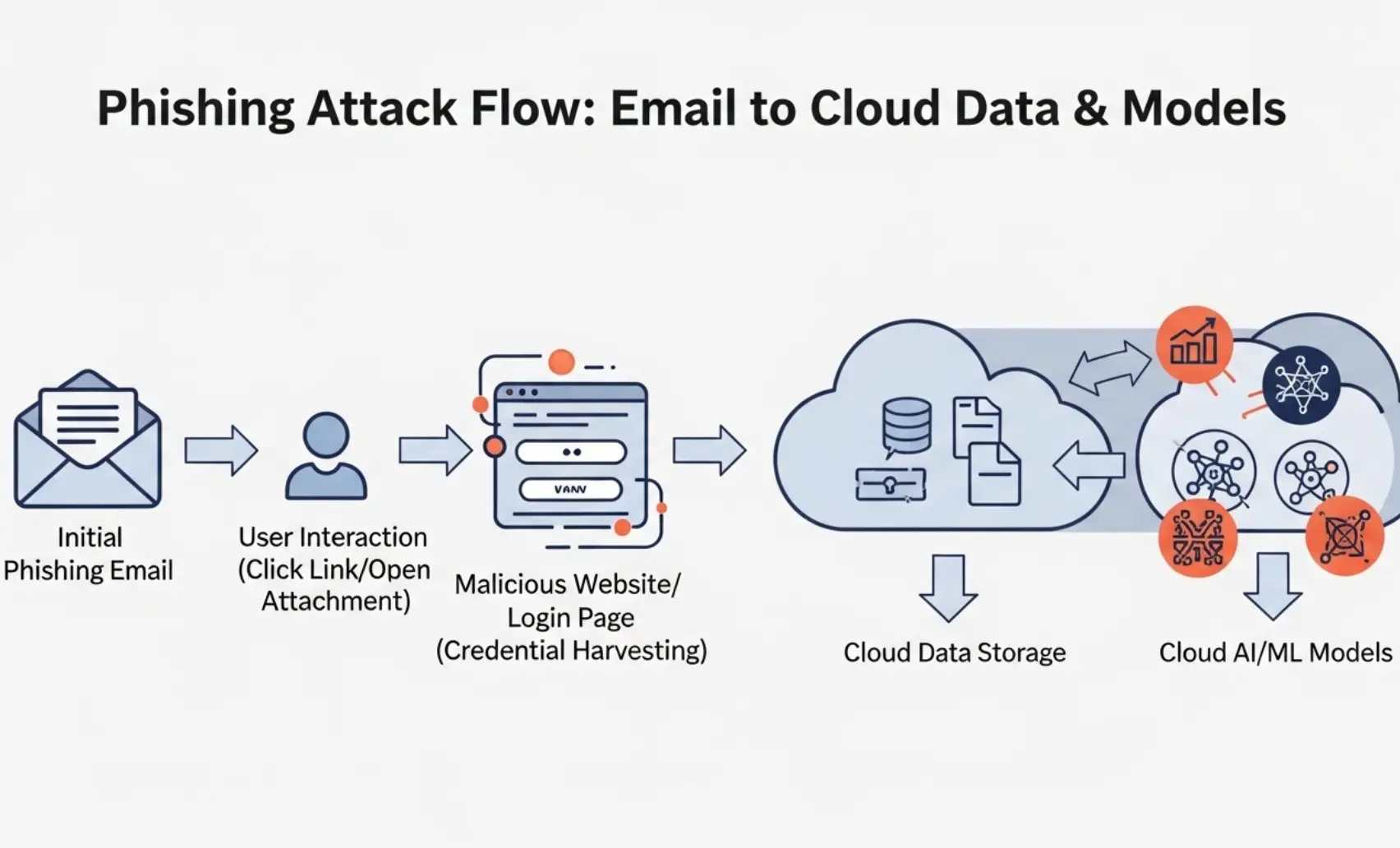
Remote and hybrid AEC environments demand a layered defense approach. The goal isn’t just compliance; it’s about keeping live design files, BIM models, and client data secure while maintaining productivity. Below are essential cybersecurity best practices for AEC remote teams based on NIST CSF 2.0 and CIS Critical Security Controls.
Access should never be universal. In distributed AEC setups, implement role-based access control (RBAC) so each architect, engineer, or subcontractor only reaches the data relevant to their task.
Action points:
Human error drives many incidents. Most breaches come from simple mistakes, clicking a phishing link, or using weak passwords. Continuous training keeps virtual engineers and BIM teams alert.
Action points:
AEC firms depend on cloud tools like Autodesk Construction Cloud, Revit Cloud Worksharing, and shared drives. The right configuration determines whether they’re secure or exposed.
Action points:
Distributed AEC teams often use personal laptops or BYOD setups. Without endpoint protection, these devices can serve as gateways for attacks.
Action points:

Autodesk, Slack, and Teams are powerful and risky if permission sprawl.
Action points:
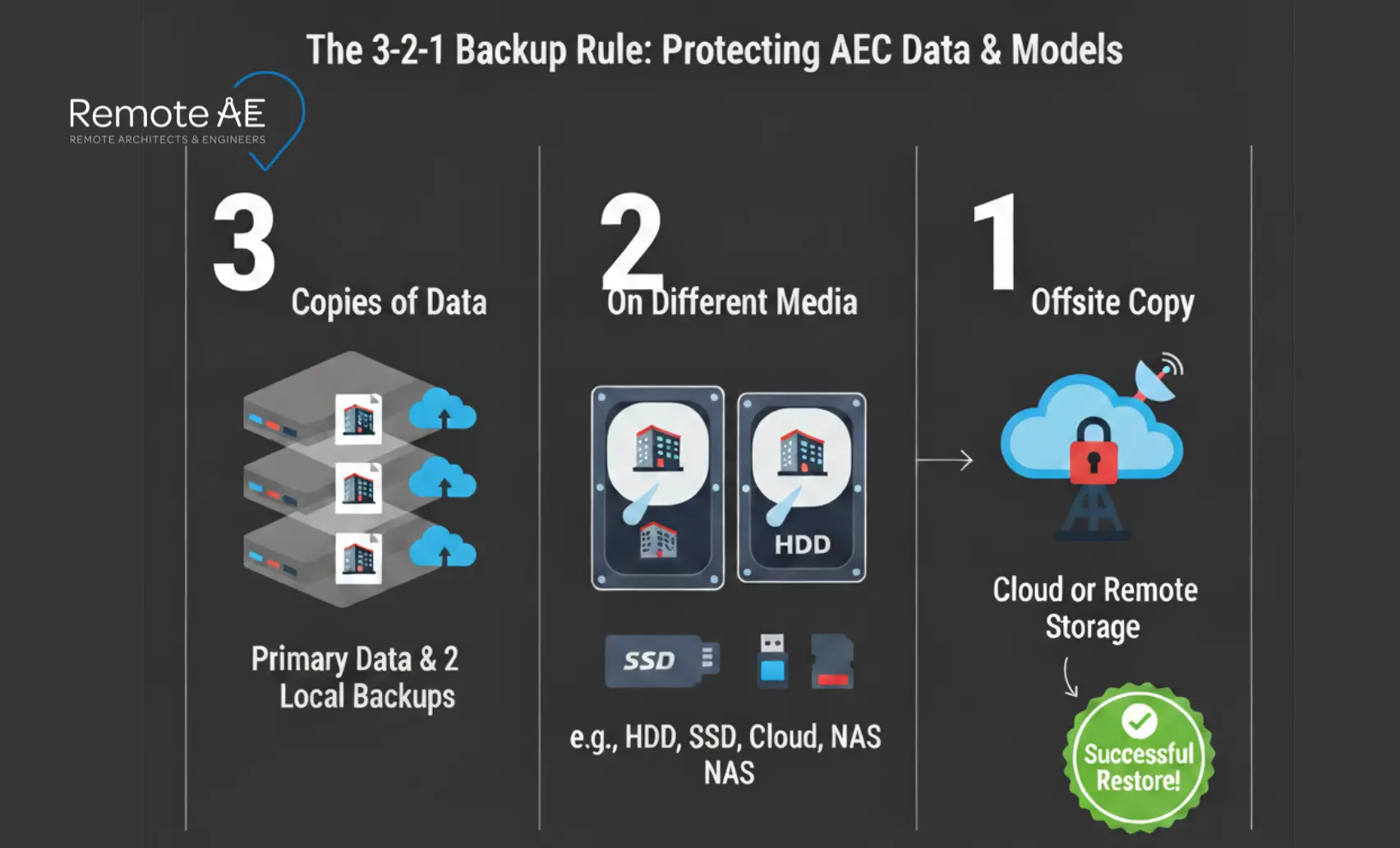
Ransomware can pause a project. Keep 3-2-1 backups (three copies, two media, one offsite). Store snapshots in separate accounts/regions so malware can’t reach them. Test restores, not just backups, every quarter and script a ransomware recovery plan that covers who declares, who communicates, and how you stage clean data. IC3 notes ransomware’s continued impact; construction-targeted writeups echo growth in extortion.
Your firm’s cybersecurity is only as strong as your weakest partner. Every subcontractor, outsourcing vendor, or remote assistant accessing your Common Data Environment (CDE) must follow the same security standards.
Action points:
Proactive monitoring helps AEC firms catch threats before they escalate.
Action points:
Even with robust defenses, breaches can still happen. A defined incident response plan guarantees you react fast, limit damage, and maintain control.
A documented incident response plan aligned with CISA and NIST guidelines can save thousands in downtime and restore trust quickly.
Remote AE isn’t just about remote staffing; it’s about secure collaboration. Every virtual professional we deploy follows strict cybersecurity protocols, built around confidentiality, compliance, and reliability.
Our commitment includes:
Remote AE helps AEC firms scale with confidence, knowing every model, drawing, and document remains protected.

You don’t need a bigger perimeter; you need the right habits, tools, and people. Remote AE helps AEC firms harden virtual teams without slowing delivery. Partner with Remote AE to build a cyber-resilient remote team for your AEC projects. Secure collaboration. Certified professionals. Global support.
Even small firms can apply the NIST Cybersecurity Framework (CSF) 2.0 by focusing on the five core functions: Identify, Protect, Detect, Respond, and Recover. Start with a simple risk register, define asset ownership, enforce MFA, and schedule regular backups. The goal is maturity, not perfection.
Yes. SSO and MFA protect identity, but a VPN protects data in transit and limits access to internal resources. Use both for layered security, SSO for user access control, and VPN for encrypted connectivity.
The top incidents include phishing, ransomware, and business email compromise (BEC). Attackers often exploit weak password hygiene or open file shares. Regular awareness training and email filtering can reduce these risks significantly.
Follow CIS Control 11: test backups quarterly and after major system changes. Always store a clean offline copy of Revit and ACC models to prevent ransomware encryption from spreading.
Other articles you may like: